Flipper Zero
It's as close as you can get to a real sonic screwdriver

After some of my friends attended Orlando B-Sides earlier this year and attended a conference about car fob hijacking, they let me know of this really neat multi-tool. I dabbled with a Proxmark 3 and some student (and professor :>) HID iClass ID cards in the past, and this little device can do exactly what I learned from that and many others things.
The Flipper Zero is a neat gadget with an absolute ton of features, but at its core its mainly a device that specializes in replay attacks (but again, it can do so much more!)
So what exactly can it do?
Well for starters, it's all open source, so it can theoretically do countless things. But for pre-installed tools, I'll just go down the menu.
It can read and emulate Sub-GHz signals, so it can replay signals for things like smart home appliances (like bulbs, thermostats, ceiling fans, door knobs, etc), Vehicle car fobs, restaurant pagers, and even the large gas station pricing signs you see when driving.
It can read and emulate 125 kHz (low proximity) RFID, so it can replay and act as RFID cards to fool things like door scanners, smart safes, etc.
It can read and emulate NFC (high proximity), so it can replay and act as an NFC card to do similar things it can do with RFID, but even read the data on credit cards (such as the full number, name, expiration date/year, etc) and then EMULATE those cards at any chip tapping payment system (like a gas station, vending machine or parking meter). Although, in order to gain that emulate functionality, you will have to dig for it, as the most common community (and official) firmware remove the ability to do it, and even remove some of its reading capability, such as removing the ability to list the name or expiration date on the card, for legal reasons. But if you're savvy enough, you can just program that functionality back in.
It has bluetooth capability, you can connect the Flipper Zero to a phone or computer for wireless capabilities.
It can read and emulate Infrared signals, so you can train it to become a universal TV or AC remote.
It can read and emulate iButton a common smart key people use to open things like community gates and doors.
It has GPIO so you can connect it to your own fancy gadgets via an arduino, breadboard, or its WiFi dev board (more on that later)
Finally, it also has bad USB functionality. You can connect it to a computer via a USB C cable and it can act as an HID (human interface device) to quickly type in keystrokes onto a computer.
All of this, and you can essentially have unlimited payloads on the Flipper as you're only limited by the size of the microSD card you use.
There still is many more features the device has (like a music player spectrum analyzer, fuzzers, weather station, metronome, calculator, keyboard + mouse, and a lot more) but I'll stop here before I go overboard.
Getting The Flipper Ready
I got the Flipper alongside its orange silicon case and the WiFi dev board.

I haven't used the WiFi board yet, but using it you can install the WiFi marauder firmware, which allows you to sniff packets among other attacks (such as deauthing or probe attacks).
Once you give the Flipper a microSD card, you can immediately install the firmware, you just need the qFlipper software to do so. It has the coolest UI as well, so it's a treat to use.

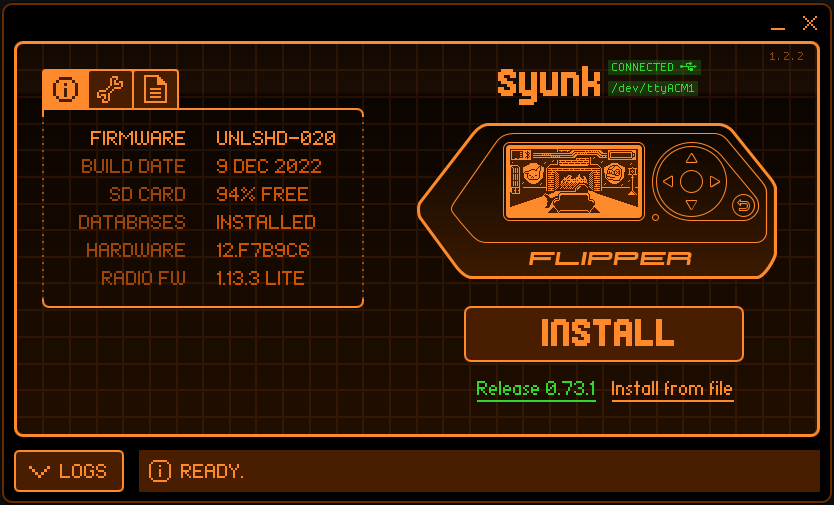
qFlipper allows you to fully interact with the Flipper as well as download from and upload to its internal storage. Here's what the interaction screen looks like:
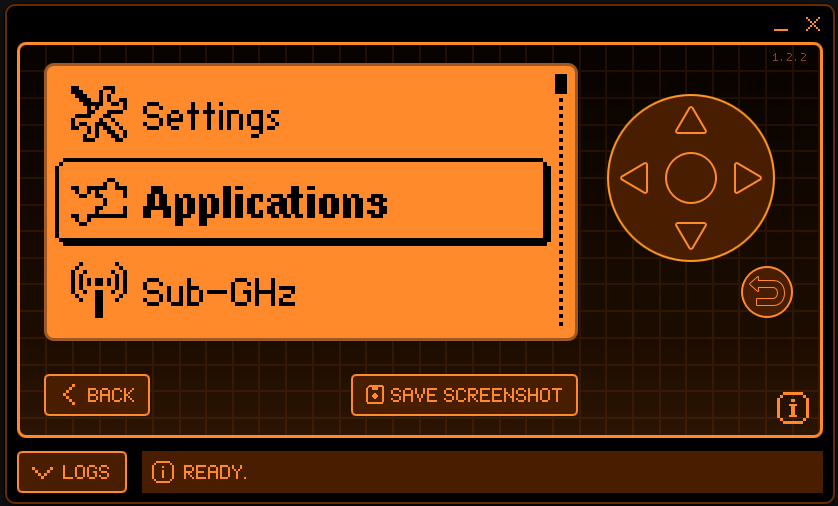
So you pretty much can do everything your flipper can do but from your computer instead.
You can choose to install the official firmware, right then and there, or you can install community firmware (which has more features). I of course did the latter and installed the Flipper Unleashed firmware. Just download the tarball from their github at
and choose 'install from file' on qFlipper. If you'd like you can install some pre-made payloads and basic applications from the github as well.
Using the Flipper
Since the Flipper can do a bajillion things, I'll focus on the NFC and Sub GHz replay attacks for now. The Bad USB functionality is essentially the same as what I discussed over in my post about the O.MG cable: https://river.rip/blog/o-mg-cable/
Before installing the firmware (either official or unleashed), the NFC reader could read my credit card's number, my name, expiration date, and UID. Now it just reads the UID and number (and can't emulate it).
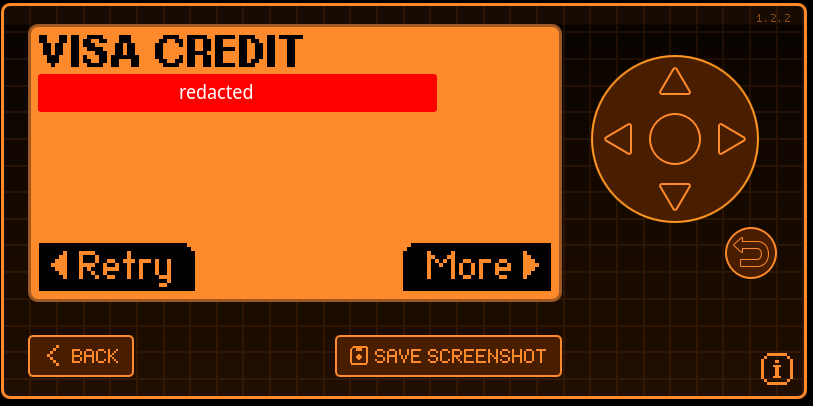
If I cared enough to be a bad boy, I could regain that functionality either by programming it myself or by finding firmware that still has it.
For the Sub GHz functionality, I can showcase it by using my car fob. Setting it to the american car frequency of 315, turning on record and clicking the car fob visibly shows that the signal was captured.
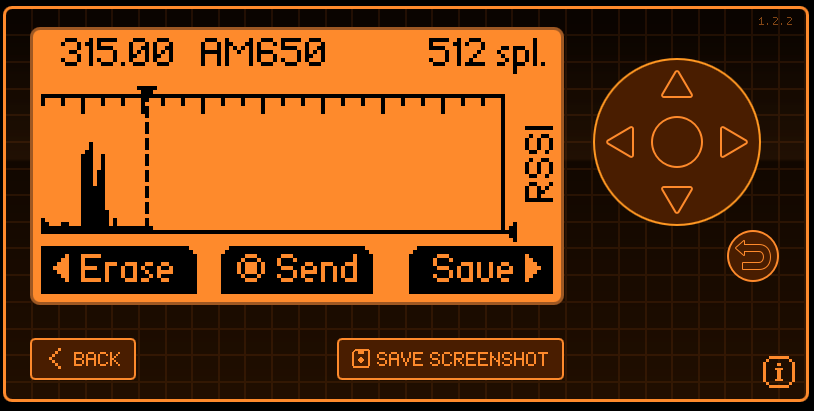
This can then be sent by pressing the center button.
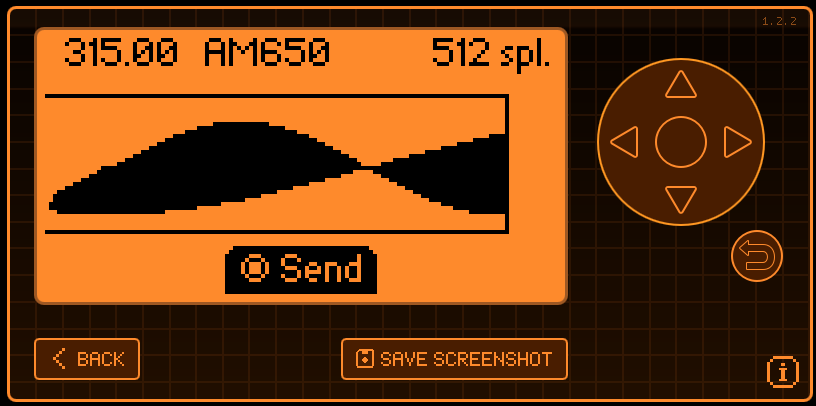
Should a car fob not have rolling keys, this would be enough to lock/unlock the car. However, they usually do. This means that on the nth time a car fob is used to unlock a car, the car is also on the nth key, so the car and fob are synced. However, everytime the fob is used, the key is moved to n+1. Capturing this signal only captured the nth signal, not the n+1 signal, so it would no longer work to unlock/lock the car.
Getting past this is pretty complicated but a good way of doing so is using the Rollback attack. Here is a neat presentation from Black Hat about it if you're interested in car fob hijacking:
https://i.blackhat.com/USA-22/Thursday/US-22-Csikor-RollBack-A-New-Time-Agnostic-Replay-Attack.pdf
I wouldn't recommend doing random replay attacks on even your own car fob, as doing so can desync your car fob from your car, effectively rendering it useless. You'll end up having to get a new car fob or going to a locksmith/dealer to get your fob fixed. Not worth it IMO.
You can find a ton of payloads, applications, plugins, firmwares, and other things over on this great github page:
But I think that's all I want to get into right now. This thing is seriously powerful and has become a viral sensation, with videos about it racking up millions of views. This of course has caused it to go mainstream, with alot of rando's ending up with it. Will that mean they'll do anything beyond playing with it once or twice and forgetting about it? Who knows. But if you want more material about it, I'd recommend this video:
P.S.: Flipper is also working on their next iteration, the Flipper One, which I most likely will get once it comes out. It seems to be a small computer all in itself, with all of Kali Linux on it.




