O.MG Cable
The funny cable

This is something I was looking to get for almost the entirety of time in University. But, being a university student, I never really had the money to just drop on a $200 USB C cable and $40 for the mandatory programmer and the malicious cable detector.
But eventually, I got around to buying it.
I got all three of these things from Hak5.
The O.MG Cable is a hand made USB cable with an advanced implant hidden inside. It is designed to allow your Red Team to emulate attack scenarios of sophisticated adversaries. Until now, a cable like this would cost $20,000
All three of these pieces of hardware were designed by a company named Mischief Gadgets and, specifically, a dude named O.MG. There are quite a few different forms of cables you can choose from, from USB C to USB A, USB A to Lightning, USB A to Micro USB, etc. It depends on what you're looking to test. Each type has 3 different tiers, however. The basic, plus, and elite. The one I have here is the elite tier, which has the following capabilities:
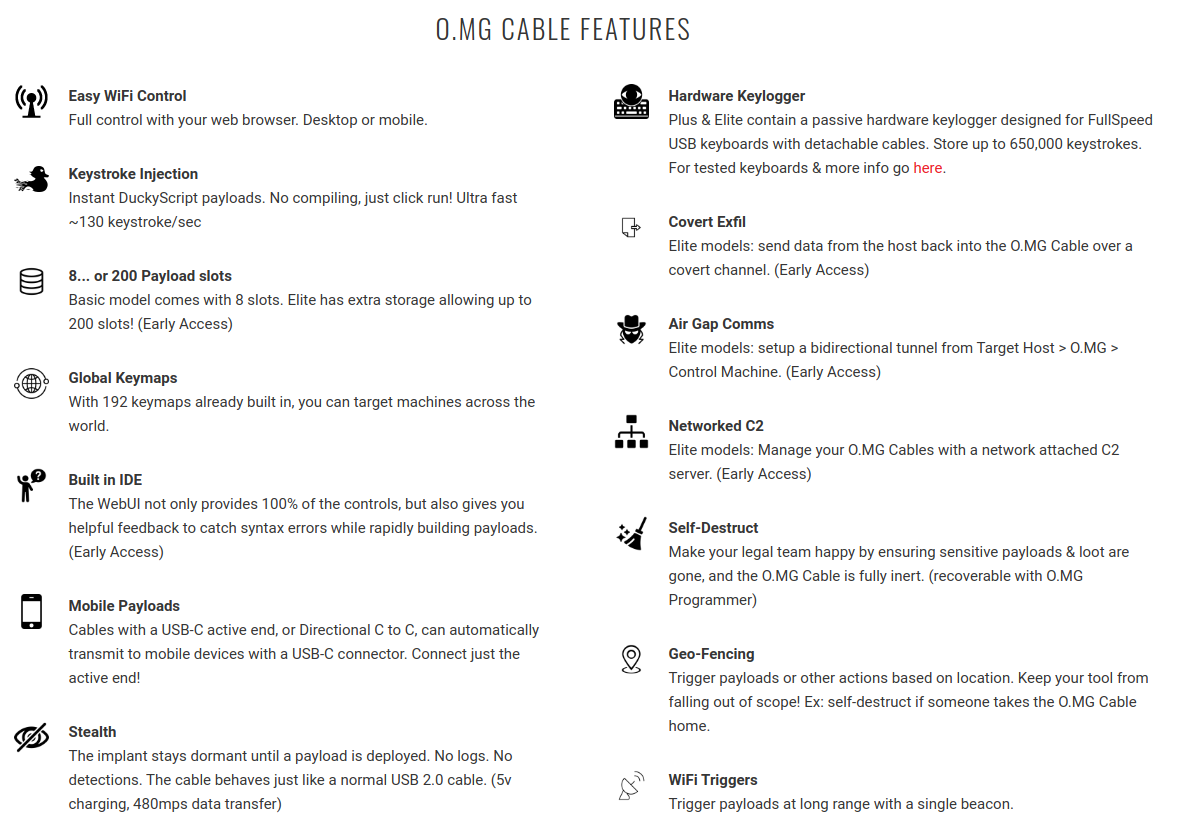
Features marked early access indicate that the firmware needed for them is in early access and will be released in 2023.
But even disregarding those specific early access features, the rest are very interesting, particularly the keystroke injection and keylogging.
The specific type I got was a USB C to USB A, with the USB A end being the active end. This means that in order for the cable to actually function, the active USB A end must be connected to the victim device. Connecting a phone or laptop to the USB C end wouldn't cause anything to happen beyond normal USB C cable functionality.
Let's look at the differences between the O.MG cable and some other normal USB C cable I had lying around. The O.MG cable came with a 3D printed orange marker, just to differentiate it from other cables.
Differences VS a Normal Cable
The first difference is the O.MG cable is a bit small (in length) at only 40" long.
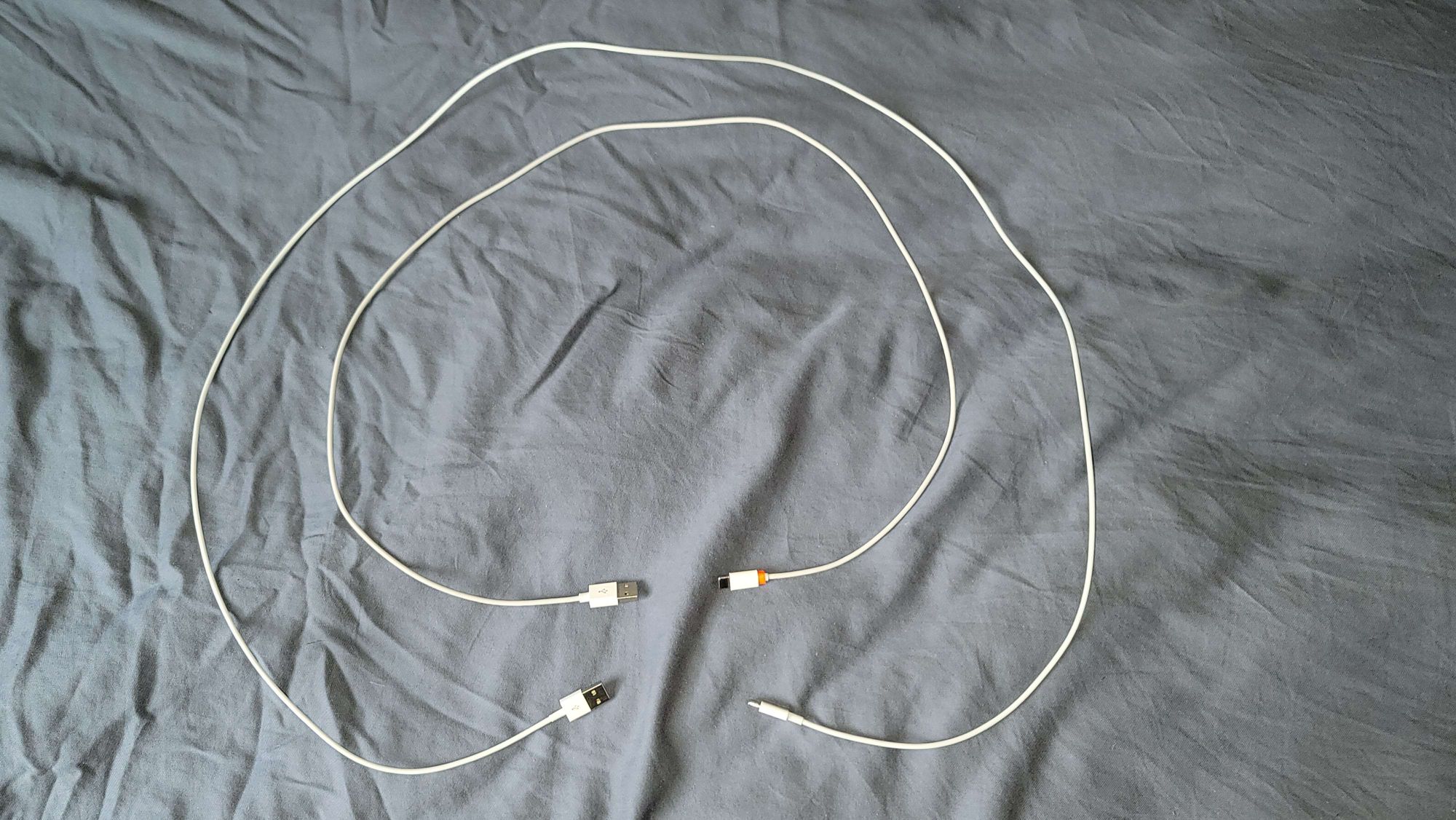
However, cables come in all sorts of lengths, so this isn't a very effective giveaway.
The next difference I could find was a seam on the C end, with the O.MG cable having a slightly larger seam.

Besides that, the actual size of the C end was identical to the normal cable.

This seam also doesn't seem very important, as the actual active end is the A connector end. Not the C connector.
Moving to the A end, the only major difference I could find between the two cables was that the O.MG cable was slightly larger.

This size difference would easily be missed by a normal user though. I know I would use a cable of this size, I'm pretty sure I've seen legitimate cables that were larger.
The only other difference was a visible seam on the O.MG cable's A connector.

The O.MG cable seemed to have a strange seam on the active A end, not visible on the normal cable. Again though, this would easily be missed by a normal user.
Using the Detector

As previously mentioned, O.MG makes malicious cable detectors. They essentially just look for activity from a USB input and lights up to let you know if it sees any. If you plug in the O.MG cable (or any other malicious cable), it'll light up. If you plug in a regular USB drive, it'll light up. If you plug in a normal cable, it won't light, as no activity was seen. However, if you connect your phone to that normal cable, it'll light up.
Here's a short video from Hak5 showcasing this:
It's not a super advanced piece of tech but it gets the job of finding malicious cables done, as normal cables (without being plugged into anything) shouldn't have any activity.
Not much more to talk about here.
Using the O.MG Cable
When actually getting the cable, you have to upload a firmware version to it. To do this, you have to buy the (sold separately) O.MG cable programmer.
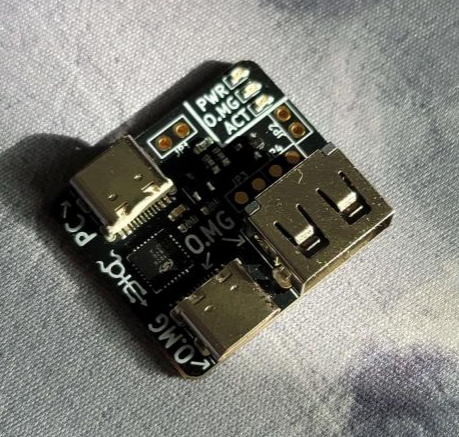
You connect the programmer to your PC with a (normal) USB C cable via the side labeled 'PC', and the active end (so in my case, the A end) of the O.MG cable to the side labeled 'O.MG'. You then have to go their online web flasher to upload the firmware.
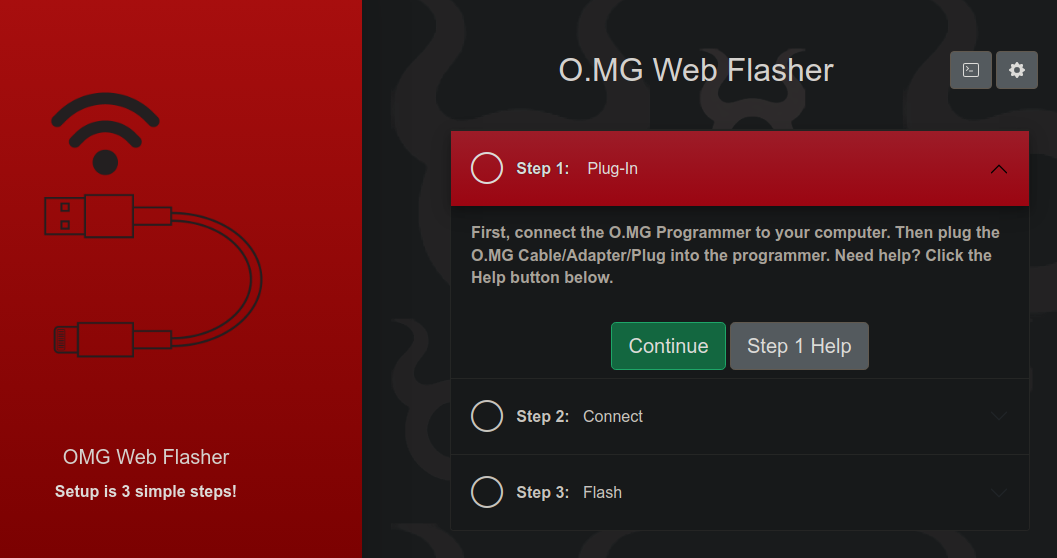
After that though, you're good to go.
Once plugged into a device, the cable creates its own WiFi network that you can connect to. By default, it's called O.MG but I renamed it to something inconspicuous (Greg's iPhone).
Connect to that network with the default password '12345678' and navigate to the web server at 192.168.4.1 and you're rolling.
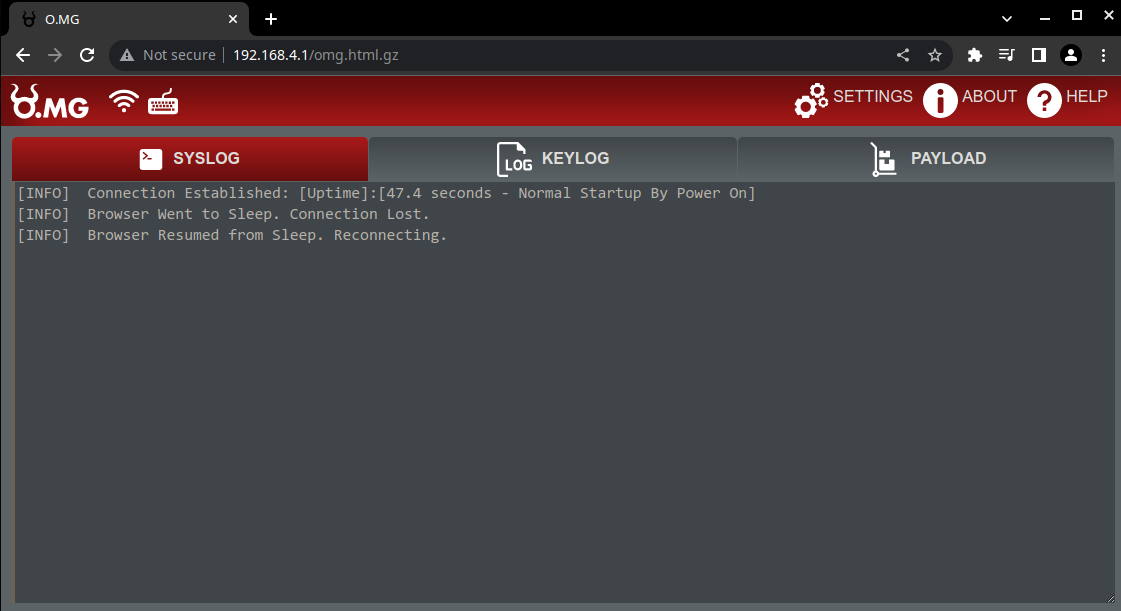
From here, you can access, create, or run stored payloads, change settings, or view the stored keylogger information. You can do pretty much anything you want here but I'll explain (in my opinion) the most interesting features, the keystroke payloads and the keylogger.
Keylogger
So the cable CAN be used as a keylogger, but with a catch. In order to keylog, you have to use the cable to connect a keyboard with a detachable cable. Yes, all my custom keyboards have detachable USB C cables that this would work with, but if you were to look to keylog a victim other than your (keyboard collecting) self, it's pretty unlikely that the keyboard being used in an office or school has a detachable cable.
To really take advantage of keyboards like that, you probably should go for the O.MG adapter or Key Croc (post coming soon™), as it can adapt a male connector (from a normal, cheap keyboard) to the host computer.
But anyways, if you do somehow get to use this cable as a keylogger on a fancy, detachable cable keyboard, you can then connect to the webUI to view all the stored keylogger information (up to 650000 keystrokes!).
Here's an excerpt from me talking with my friend after keylogging myself and forgetting about it for a week:
Pretty cool
Keystroke Injection
So this cable can effectively act like a Rubby Ducky USB (hopefully I'll have a post about that in the future). This basically means that the cable acts as a HID, or human interface device (like a keyboard, mouse, etc). Computers normally trust these devices by default, so you can plug in these malicious devices and have it run automatically, without the user confirming that they want it to like a normal USB drive would have to be.
Combine this with the fast keystroke injection (130/second) and the cable can essentially do anything a normal keyboard can do, but way faster. This can be anything from downloading a Rick Roll video, setting the volume to max, disabling the mouse, and blasting Never Gonna Give You Up to downloading and installing ransomware and exfiltrating cached WiFi passwords.
Because the cable is pretty much just a keyboard, it works on all operating systems. Windows, Mac, Linux, even Android and iOS (if you have a mobile compatible cable). You just have to adapt the payloads to OS.
The payloads are written in DuckyScript, a very simplistic scripting language with its own quirks (like having no arrays or floats/doubles). But ignoring them, it's quite powerful.
To run a payload, you navigate to the 'PAYLOAD' section in the Web UI
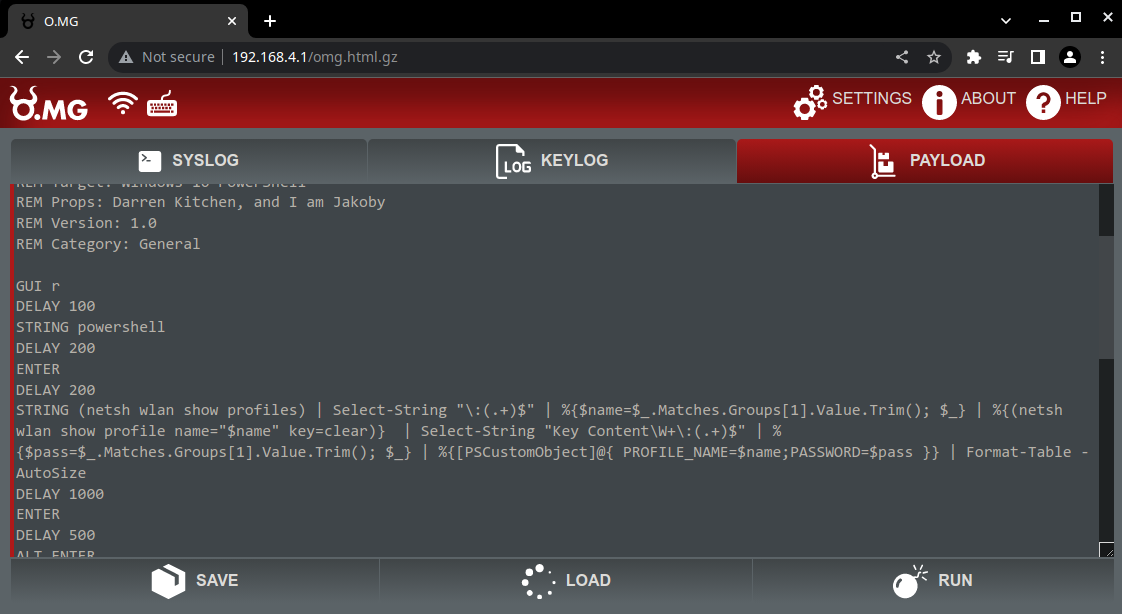
Here you can copy and paste or make your own payloads, run them or save them to a specific slot for later. You can also configure the payload to run immediately once the cable is plugged in.
That's the gist of it. This cable is a Rubber Ducky that is even more inconspicuous looking. Have you ever been told not to plug in random USB drives you've found? It's because of the Rubber Ducky. This cable does exactly that and more.
We are in a timeline where we will soon have to be cautious of not just devices like USB drives being plugged into our computers and phones, but regular old CABLES. I know I won't ever accept someone else's cable when I need a charger for my phone, lol.

